What Is a Transparent Proxy?
Whether you're an individual user seeking improved online privacy or a network administrator striving to optimize network performance and security for your organization, understanding the nuances of web proxies is crucial. Web proxies are web servers that act as a gateway between a client application and the server it needs to communicate with.
One such proxy that plays a vital role in network management and cybersecurity is a transparent proxy. Transparent proxies are used to set up content filtering and caching, protect from common cybersecurity attacks such as DDoS, and facilitate network traffic management.
In this article, you'll learn all about transparent proxies, including how they work, their pros and cons, when to use them, and how to detect if a transparent proxy is active in your local network.

Understanding Transparent Proxies
A transparent proxy, also known as an inline proxy, is a server that acts as a conduit between an end user and the internet without declaring its presence. The word "transparent" describes its nature of not modifying requests and responses. It can be installed on a network without the users' knowledge because it doesn't require any configuration on the users' side.
As mentioned previously, one of the main purposes of deploying a transparent proxy is to cache frequently accessed data locally, reducing bandwidth usage and improving web page loading times.
How a Transparent Proxy Works
When a user or device on the network makes a request to access a website or an online resource, the transparent proxy intercepts the request. This interception is often done at the network level, such as within a firewall or gateway device. This means that the proxy isn't configured on the users' devices. Instead, it's set up globally at one of the central hubs in the local network, such as a firewall, a gateway, or even a router, usually on the communication path to the internet.
For instance, if you've tried accessing a public Wi-Fi hotspot and run into an authentication page asking for your details before providing you access to the internet, that's usually a transparent proxy working behind the scenes:
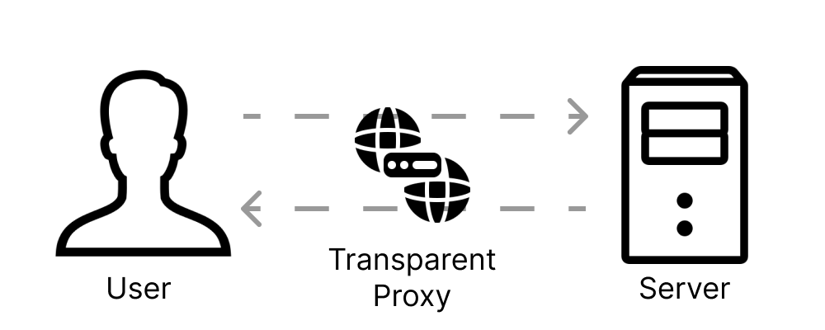
The transparent proxy sits in the middle of the user and server, without either of them knowing about it. It routes the web request to the destination server as if it were the client making the request directly. From the perspective of the client device, it appears as if the request is going directly to the web server.
After processing the request, the transparent proxy forwards the response from the web server back to the client device. Again, this is done transparently, and the client is typically unaware of the proxy's involvement.
While forwarding the request, the transparent proxy can perform various functions, such as caching frequently requested content, filtering web traffic for security or content control purposes, or modifying web content before it reaches the client.
Transparent Proxies vs. Nontransparent Proxies
One of the main differences between nontransparent and transparent proxies is that nontransparent proxies are typically implemented as standalone proxy servers or as software applications running on dedicated hardware or virtual machines. This means they often require manual configuration on client devices, such as configuring the proxy server's IP address and port.
In nontransparent proxies, users are aware that they're using a proxy server. Typically, users have control over proxy settings and can modify or bypass them if they choose. With transparent proxies, the configuration is mostly done at the network level, requiring no additional setup. This also means that a transparent proxy may be set up on a network without users' knowledge.
Pros and Cons of Using a Transparent Proxy
The following are some of the upsides of implementing a transparent proxy:
- Can improve network performance. A transparent proxy caches frequently accessed data. This reduces the time a web page takes to load and lessens bandwidth consumption, resulting in a faster network and better user experience. However, if your traffic frequently includes previously unvisited websites, this might backfire on you as transparent proxies can add latency overhead to your requests due to the additional routing needed.
- Helps filter traffic. Transparent proxies can be configured to filter web content based on predefined rules and policies. This allows IT teams to block access to specific websites or content categories, enhancing network security and productivity.
- Easy to implement. A transparent proxy is easy to implement because it does not require any configuration on the user's side. Since they are implemented at the network level, transparent proxies intercept traffic and redirect it at the network level, making them transparent to users.
- Scales easily. Transparent proxies are innately scalable, which means that adding more proxy servers or improving the already existing ones does not require reconfiguration on the client devices. This scalability is especially useful for large networks with ever-growing traffic.
There are also a few downsides you must keep in mind when working with transparent proxies:
- No privacy. Since the users are often unaware of the presence of a transparent proxy, it may raise privacy concerns. Additionally, a transparent proxy may not always conceal the user's IP address from the websites and services they are using. This means transparent proxies are not suitable for users looking for anonymity.
- Does not offer security. The one expectation of users is that their encrypted communications are private and secure. Intercepting and decrypting traffic violates the trust and privacy of the users. This might lead to both legal and ethical issues. If the proxy is compromised, attackers might get their hands on sensitive data during the decryption process.
- No benefits when scraping. When you implement a web scraping project, using a transparent proxy offers no benefit as you can still be identified and blocked. In such cases, it's best to use an anonymous or elite proxy instead.
When You Should Use a Transparent Proxy
Transparent proxies are great thanks to their easy setup and support for censoring traffic. Following are a few real-world scenarios where using transparent proxies makes sense:
- By ISPs for censoring and filtering content: Transparent proxies can be deployed for censoring and filtering content on the network. Access to specific sites and content can be blocked as needed.
- For access control: Transparent proxies often operate as a useful gateway by blocking unwanted traffic on a network. Whenever a user tries to access a website or content, a transparent proxy intercepts their requests and allows them to proceed only after verifying their right to do so.
- For load balancing and traffic shaping: Transparent proxies can allot incoming traffic across different backend servers, balancing the load and allowing efficient use of the services. This ensures reliability and service availability. Transparent proxies also enable administrators to shape or prioritize network traffic based on application or service requirements. This ensures that critical applications receive adequate bandwidth and low-latency connections.
- For DDoS protection: DDoS attacks are implemented to overwhelm a website with requests. Transparent proxies contribute to DDoS protection by acting as a filter for incoming traffic before it reaches the target servers. This is achieved by inspecting, detecting, and discarding suspicious or malicious requests (ie a large number of requests from specific IP ranges). Transparent proxies can deny requests until the security team has mitigated the attack.
- For caching web pages for faster performance: Large organizations and ISPs often use transparent proxies to cache frequently accessed content. Copies of web pages, multimedia, and images are stored locally, considerably reducing bandwidth usage and improving web page loading time.
Can You Detect a Transparent Proxy?
Detecting a transparent proxy can be challenging because they're designed to function without any configuration on the client side. However, some methods can help detect the presence of a transparent proxy:
- Changes in HTTP headers: Some transparent proxies modify HTTP headers as traffic flows through them. Examining the headers to check for the presence of any additional headers or changes in the existing ones can help detect transparent proxies. For instance, you can look for
X-Forwarded-FororX-Client-IPheaders that some transparent proxies might add to passing requests. Here is a quick tutorial you can follow that can help you detect transparent proxies in some cases. - Unusual latency: If the response for web requests is taking significantly longer, it might indicate a transparent proxy's presence. It could also indicate a number of other issues, so this is not a certain indicator of a transparent proxy.
- Deploy online proxy detection services: Many websites and online services offer APIs and proxy detection tools (such as this one) to help identify the presence of a proxy. They do so by analyzing traffic and determining if a proxy is in use. Once again, the success rate of such methods greatly depends on how well the transparent proxy has been configured (and hidden).
- Ping or traceroute analysis: Check if there are unusual routing patterns in the network path by conducting ping or traceroute tests. This might give you an idea about the presence of a transparent proxy. You could also review firewall, proxy, or network logs on your network and look for traffic redirection. However, you would still need to know the correct path that your packets would travel through if there was no proxy. Additionally, some recommend doing a traceroute on port 25 and comparing it with port 80 to see if it changes, hinting towards the presence of a transparent proxy.
- SSL/TLS certificates: You can also analyze the SSL certificates of requests originating from and being received by your client. Transparent proxies usually need to replace the request's certificates with one of their own, so this should be an easy tell. However, the IT department often adds the new certificate to your computer's certificate store to avoid having certificate errors constantly, so this method might not work in all cases.
- Analyze DNS requests: Transparent proxies often manipulate DNS requests to redirect traffic. Analyze DNS traffic and look for any such redirection that might indicate the presence of a transparent proxy.
💡 Need free proxies? Discover how to scrape fresh free public proxies with our AI-powered Web Scraping API.
Conclusion
In the ever-changing world of network technologies, a transparent proxy is a unique tool for optimizing network performance, facilitating robust content delivery, and fortifying security. In this article, you learned what a transparent proxy is, how it works, its benefits and disadvantages, when it makes the most sense to use it, and how to detect if one has been deployed in your network.
💡 Want to learn more about the different types of proxies? Check out our guide on Forward Vs. Reverse proxies


